Did Apple Passkey Just Kill Traditional Passwords?
And Will Passkeys Permanently Marry You to Apple? Humans are weak and so are our passwords. We make easily memorizable (read: guessable) passwords that accidentally invite cybercriminals and identity thieves into our homes, offices and bank accounts like a neighbor for afternoon tea. The solution? Remove humans from the tea party. Enter Apple. At the company’s annual WWDC developer conference,...
Read More
Automotive Cybersecurity: Don’t Bank on Untrained “Drivers”
Would you send your newly licensed 16-year-old out to drive on the interstate without spending months teaching them safety skills and the rules of the road? I hope not! Even if their car had all of the latest safety technology - front and side airbags, auto-locking seatbelts, crash-warning sensors - and a low-deductible insurance policy, you still wouldn't take the...
Read More
Anonymous vs Russia Hacktivism for Ukraine
Who thought that Anonymous vs Russia would be the top billing cyber event of the Russian invasion of Ukraine? We watch in horror and disgust as Russia continues its assault on the Ukrainian people. Tanks roll down streets, missiles are launched, neighborhoods are shelled and innocent civilians are killed. Some things never change in war. As each new conflict begins...
Read More
Hackers Hot for Hotspots: Protect Your Remote Workforce
Your remote workforce is only as strong as its weakest link — which, believe it or not, may be a public WiFi hotspot. Insecure networks have been at the forefront of a recent spike in business-impacting cyber attacks, namely among organizations that have deployed a remote workforce who accessed malicious WiFi networks or hacker-enabled hotspots. Have we become so dependent...
Read More
Face Computers: Privacy Violation by Pupil Dilation?
Smartwatches, holograms, self-driving vehicles — we may have just rung in the year 2022, but here on Earth, we’ve started to live (blindly) like the Jetsons in 2062. The latest technological advancement coming out of Orbit City, err, Silicon Valley is the face computer, wearable tech that will plunge users into the notorious “metaverse.” Just saying the word metaverse makes...
Read More
Ransomware Attacks in 2022: What You Need to Know
Every company is vulnerable to cyber attack — and I mean every company, small and large. Are you responsible for delivering half of the East Coast’s fuel supply? Vulnerable. Are you the largest beef supplier in the world? Yep, still vulnerable. The alarming surge in ransomware attacks has put a target on every company’s back, including massive organizations like Colonial...
Read More
Ransomware Attack: What if this were your Billion $ mistake?
No one has ever heard of your company. Let’s call it, COMPANY X. And you like it that way. In 57 years, you’ve never once shut down your mission-critical operations that fuel the US economy. YOU are an honest, satisfied employee of Company X, and although your security team hounded you with preachy posters in every ELEVATOR to never use...
Read More
New iPhone Setting Stops Apps & Ads from Stalking You (App Tracking Transparency)
Apple App Tracking Transparency is Finally Here! With the release of iOS 14.5, Apple has given us the most powerful privacy tool for users in many years - it's called App Tracking Transparency (ATT). The update also includes a lot of features that have Apple product users very excited, like new Siri voices and being able to open your iPhone...
Read More
Facebook Breach: Zuckerberg Karma & Your Stolen Cell #
The Facebook Breach Might Not Be What You're Thinking How many Facebook user records were just breached? The answer might surprise you. Zero. That's right, the 533 million records that were "scraped" off in the recent-headline-grabbing Facebook breach actually disappeared from their website in 2018 and 2019. Not 2021. It's just that Facebook never told us. Never notified us per...
Read More
SolarWinds Hack: What Vladimir Putin Wants Every Business To Ignore
Summary of the SolarWinds Hack Russian hackers inserted malicious code into a ubiquitous piece of network-management software (SolarWinds and other companies) used by a majority of governmental agencies, Fortune 500 companies and many cloud providers. The software potentially gives Russia an all-access pass into the data of breached organizations and their customers. Immediate Steps to Protect Your Network I would...
Read More
Nancy Pelosi Laptop Stolen for Sale to Russia by Capitol Rioter
And my prediction about the hidden risk in the capitol riot appears to be coming true... "There are growing concerns that U.S. adversaries may be seeking ways to benefit from the Capitol assault – and that some of rioters may have been looking to work with them. The FBI is investigating claims that Riley June Williams stole a laptop or or...
Read More
Is WhatsApp Privacy a Big Fat Facebook Lie? What You Need to Know.
WhatsApp Privacy: Facebook's New "Data Use" Policy I have been getting a ton of questions on the privacy of your personal data that is sent through WhatsApp. Is Facebook, who owns WhatsApp, sharing everything you write, including all of your contacts, messages and behaviors? It’s not quite that simple, but neither is Facebook. Facebook announced a new WhatsApp privacy policy...
Read More
The Massive U.S. Capitol Attack We’re Ignoring
https://www.youtube.com/watch?v=dIdPk25c93M' format='16-9' width='16' height='9' custom_class='' av_uid='av-mo9up3' Capitol Attack Could Go Way Beyond a Physical Breach When Trump supporters occupied the US Capitol last week, hundreds of rioters gained unrestricted access to the offices of our Representatives and Senators . You can see one such invader sitting here in House Speaker Nancy Pelosi's office. But we have to ask ourselves, did...
Read More
Twitter Hack Reminds Us That David Can Still Fell Goliath
The twitter hack began as a quiet scheme to steal and sell unusual user names, which carry high currency in gamer and hacker circles. But as the day wore on, the attack took over dozens of accounts belonging to corporations like Apple and celebrities like Joe Biden, Barack Obama, Bill Gates, Elon Musk and Kanye West. The hackers used the...
Read More
Were Lebron’s Darkest Secrets Exposed by Hackers?
Grubman Shire Hack: REvil Scores a Blackmail Slam Dunk How much is basketball megastar Lebron James brand worth to hackers? When you calculate it, Lebron's name earns him more than his game. And to the cybercriminals who orchestrated the Grubman Shire Hack, that kind of payday is worth jumping through some hoops. Consider what James makes off of his reputation...
Read More
Don’t Be Naive: Obama/Biden “Twitter Hack” Not What It Seemed
I'm betting that the recent Twitter hack of prominent political and celebrity Twitter accounts was politically motivated and nation-state operated. But that's not what "the investigators" say. And that false narrative could have massive implications for your privacy. Here's the background in a nutshell: Approximately 130 high-profile Twitter accounts were hacked on July 15 in what the company is...
Read More
Cybersecurity Experts Fight for Your Encryption Rights
Cybersecurity experts and privacy advocates like myself are stepping up to protect strong encryption standards, which are facing an all-out legislative assault from the current administration and the Senate. But we need the help of business leaders like yourself to maintain the privacy of your data. Here is an excellent excerpt from Joseph Marks of The Washington Post: “The bill, called the...
Read More
iPhone Security Crash Course: 13 Hacker-proofing Tips
iPhone Security In the Mid/Post-Pandemic World We are no longer just addicted to our iPhones; we are officially in a committed relationship, thanks to the pandemic. We mobile office from them, bank from them, attend doctor’s appointments, kids' classes and Zoom happy hours from them. And in the midst of all of this critical and effective use, we are...
Read More
Coronavirus Scammers User Fake Sites to Steal Your Stimulus
https://www.youtube.com/watch?v=WJcT81kawc4' format='16-9' width='16' height='9' custom_class='' av_uid='av-mo9up3 Coronavirus Scammers Are After Your Stimulus Check Scammers and cybercriminals love to exploit the headlines. COVID-19 isn't the only pandemic affecting Americans - so are the scams that go along with it. Case in point: stimulus checks that will help Americans weather the COVID-19 pandemic are already being targeted by scammers, who take advantage...
Read More
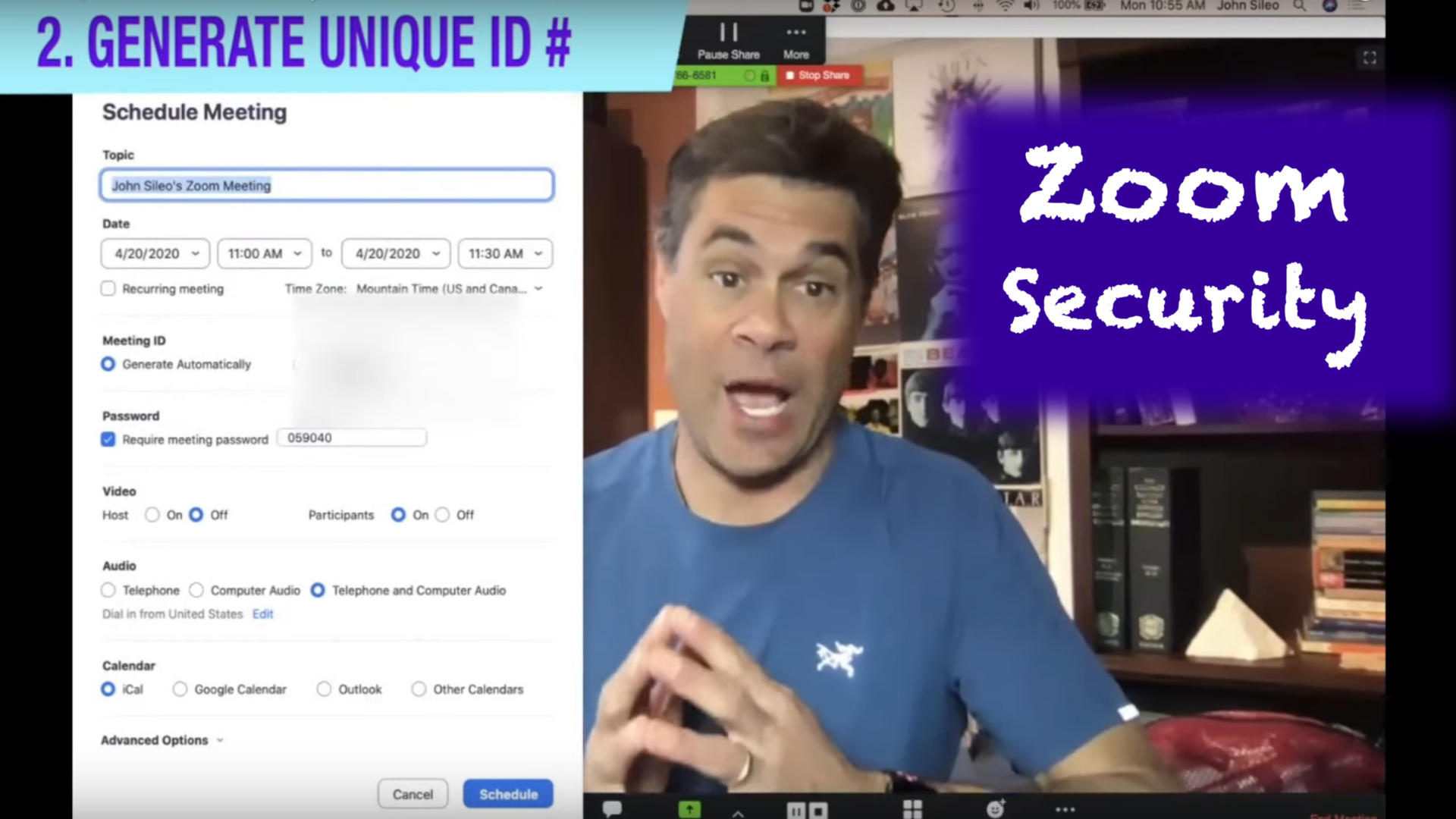
Zoom Security in 7 Steps (Video + Graphic)
https://www.youtube.com/watch?v=CTDjDCiI9Hc' format='16-9' width='16' height='9' custom_class='' av_uid='av-mo9up3 Since this video was recorded, Zoom has issued several security updates. Learn more at the Zoom Security web page and don't forget to update to the latest version! Zoom Security Transcript: Hey, everybody. It's good to see you back again. Today we're going to talk about seven steps you can take to lock down...
Read More